Decoding Huawei Cloud Security's 'Iron Triangle': Conquering Security Challenges with 'Layered Defense'
![]() 08/08 2025
08/08 2025
![]() 806
806

In recent years, data security threats have become all too common.
In April 2024, a domestic cloud service provider faced widespread service failures, including interface response errors and internal service disruptions, resulting in 1,957 customer complaints within 87 minutes.
In September 2024, users reported that creating a new folder in a 'Cloud Disk' service from another domestic provider automatically loaded private photos belonging to strangers.
In June 2025, CyberNews disclosed the 'largest data breach of 2025,' involving 30 databases with a staggering 16 billion login credentials, affecting numerous domestic and international cloud vendors, enterprise platforms, and developer portals.
In the real world, where 'network security breaches equate to business disasters,' enterprises increasingly recognize that security is not merely an IT department task but a strategic cornerstone that determines their survival. Especially in the current era of widespread AI applications and deep-rooted intelligent transformation, the strength of security capabilities directly shapes the depth of an enterprise's digital and intelligent transformation, influencing brand image, customer trust, and business continuity.
Therefore, enterprises urgently need a systematic, intelligent, and forward-thinking security protection architecture: one that not only 'sees' risks but also 'predicts' threats; not only 'defends against' known attacks but also 'uncovers' unknown intentions; and, importantly, 'responds in coordination' to automatically block threats before they cause significant damage.
To address these needs, Huawei Cloud offers compliant, efficient, and stable security services. Especially in high-frequency security risk scenarios such as network boundaries, hosts, and web applications, it leverages professional products like Cloud Firewall (CFW), Host Security Service (HSS), and Web Application Firewall (WAF) to create an integrated security protection system encompassing awareness, prediction, defense, and response, embedding security capabilities throughout the business lifecycle.
A Gartner study predicts that 85% of enterprises will 'go to the cloud' by 2025. However, another report reveals that 80% of enterprises have encountered cloud-related security incidents.
For example, DDoS attacks, which are frequently heard of, can involve hundreds of gigabytes or even terabytes of traffic, overwhelming traditional hardware firewalls. Additionally, unauthorized access exploiting application logic vulnerabilities can bypass traditional boundary defenses, silently stealing data within the intranet.
Huawei Cloud's solution is Cloud Firewall (CFW), serving as the 'main gate' for cloud traffic, safeguarding enterprises' internet boundaries and VPC boundaries with capabilities such as asset management, access control policies, attack defense, and antivirus.
Firstly, it prevents external intrusions, keeping threats at bay.
As enterprises open internet services to users, they also face malicious scanning and attacks from outside. Especially concerning are 0-Day vulnerabilities (security flaws discovered before official patches are released) and their variant attacks, which conventional static rule libraries struggle to defend against promptly and effectively.
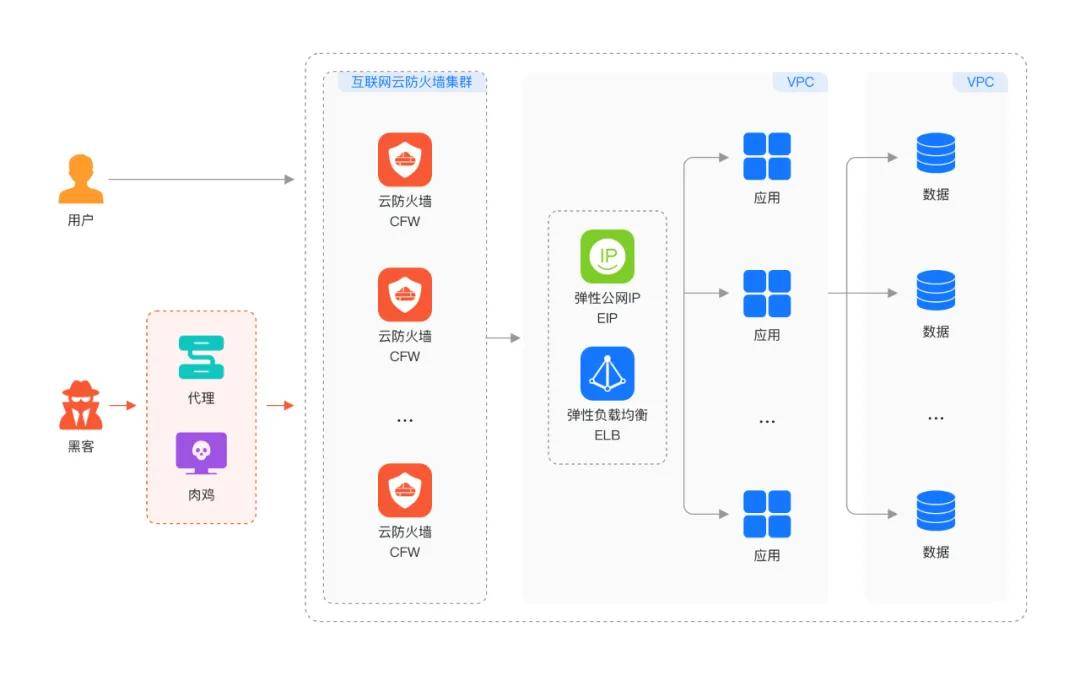
Huawei Cloud CFW revolutionizes the past model where users had to manually configure complex rules, integrating Huawei's global threat vulnerability library to enable intrusion detection and defense with just one click. It supports over 12,000 IPS signatures, along with antivirus, anti-shellbounce, sensitive directory scanning, custom IPS, and other protections.
Moreover, CFW can coordinate with various cloud services, such as Security Brain (SecMaster) for real-time firewall log collection and Cloud Trace Service (CTS) for real-time monitoring and auditing, minimizing asset threats and risks.
Secondly, it implements active outbound control, accurately identifying 'insiders.'
News often reports cases of 'employees using company servers for mining,' causing direct economic losses and potentially leading to security vulnerabilities due to 'unconventional means.' Effectively preventing and detecting servers from being 'mined' has become a critical requirement for cloud firewalls.
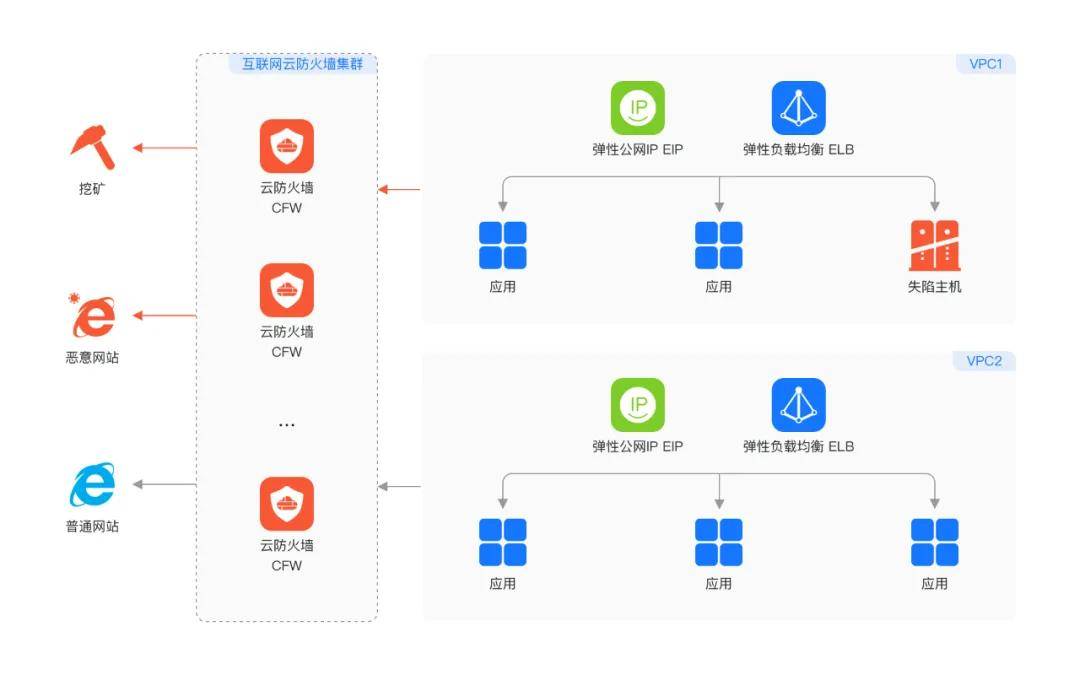
Huawei Cloud's answer is the active outbound control function, performing in-depth analysis on all outbound traffic based on Huawei's global threat vulnerability library. Once a server attempts to connect to known malicious addresses or engages in 'mining' behavior, it assesses the compromised host's risk status, blocks malicious linking in real-time, and immediately generates an alarm to help operations and maintenance personnel quickly locate and clean up the problematic host.
Thirdly, it manages inter-VPC access control, preventing 'domino effects.'
Many enterprises have multiple VPCs on the cloud, interconnected through peering connections, cloud connections, etc. The rapid growth of data and connection requirements has made controlling 'east-west' traffic between VPCs extremely complex. If a single VPC host is compromised, attackers can launch lateral penetration attacks on other VPCs.
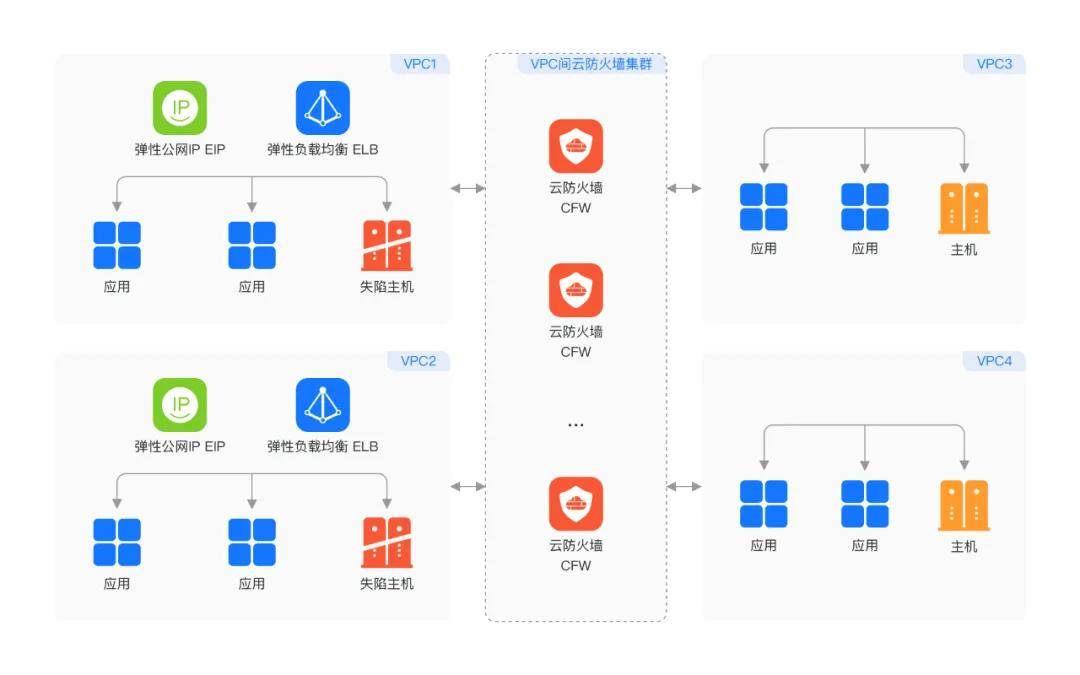
Huawei Cloud CFW enables access control in complex, high-traffic scenarios such as between VPCs and between VPCs and local data centers, preventing lateral threat penetration by defining refined access control policies. For instance, using the cloud firewall to achieve micro-segregation of traffic between VPCs ensures complete access control for business systems, identifies and blocks malicious access, limits the attack scope to the smallest unit, and ensures the security of core data assets.
Numerous scenarios could be listed.
To use an analogy, the cloud firewall functions like the enterprise's 'intelligent security center,' equipped with a diligent security team and an unbreakable technological wall, strictly controlling who can enter and exit, immediately reporting and blocking abnormal personnel or suspicious items, transforming the passive situation of traditional security protection.
If the cloud firewall is the 'wall' guarding enterprise asset security, the enterprise host, as the unit for data processing and storage, represents the 'last meter' of system security.
Countless enterprises face this dilemma: system logs frequently alert about abnormal logins with no discernible cause, silent malicious processes stealing data, high-risk vulnerabilities left unpatched that hackers can exploit at any time, and arbitrarily opened ports providing potential entry points for attackers. The challenge lies in these problems often occurring within the system, making them difficult for traditional network layer defenses to detect.
When enterprises grapple with system security concerns, Huawei Cloud addresses them through the Host Security Service (HSS), providing core functions such as asset management, virus detection and removal, intrusion detection, ransomware prevention, and webpage tamper-proofing, presenting a novel solution for proactive prevention, in-event defense, and post-event response.
Taking four typical host security scenarios as examples, Huawei Cloud offers precise response solutions.
Firstly, ransomware protection.
Ransomware has always been a nightmare for enterprises, with consequences ranging from business disruptions to complete data loss upon infection.
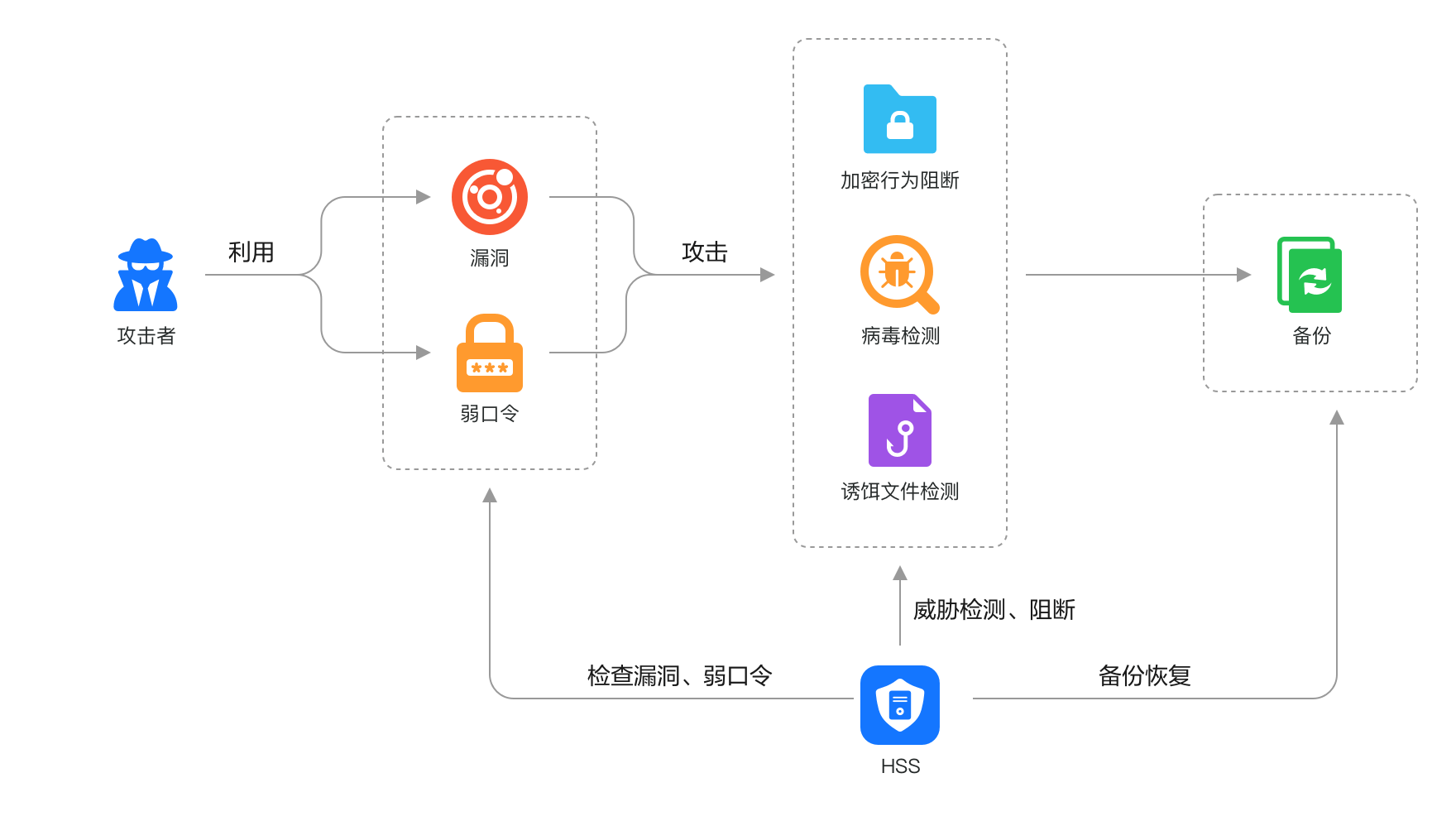
Huawei Cloud HSS pioneered a triple ransomware detection engine combining 'preventing intrusion, encryption, and proliferation,' based on precise intelligence, AI, characteristics, and behavior detection. It intercepts known ransomware in real-time, currently covering 99% of known ransomware families, providing rapid automated blocking, isolating abnormal ransomware processes and files, swiftly halting ransomware encryption and proliferation, and offering ransomware backup recovery capabilities to mitigate business damage.
Secondly, webpage tamper-proofing.
Imagine a scenario where hackers invade a server and silently replace official website files for users to download, directly impacting the enterprise's financial security and brand image.
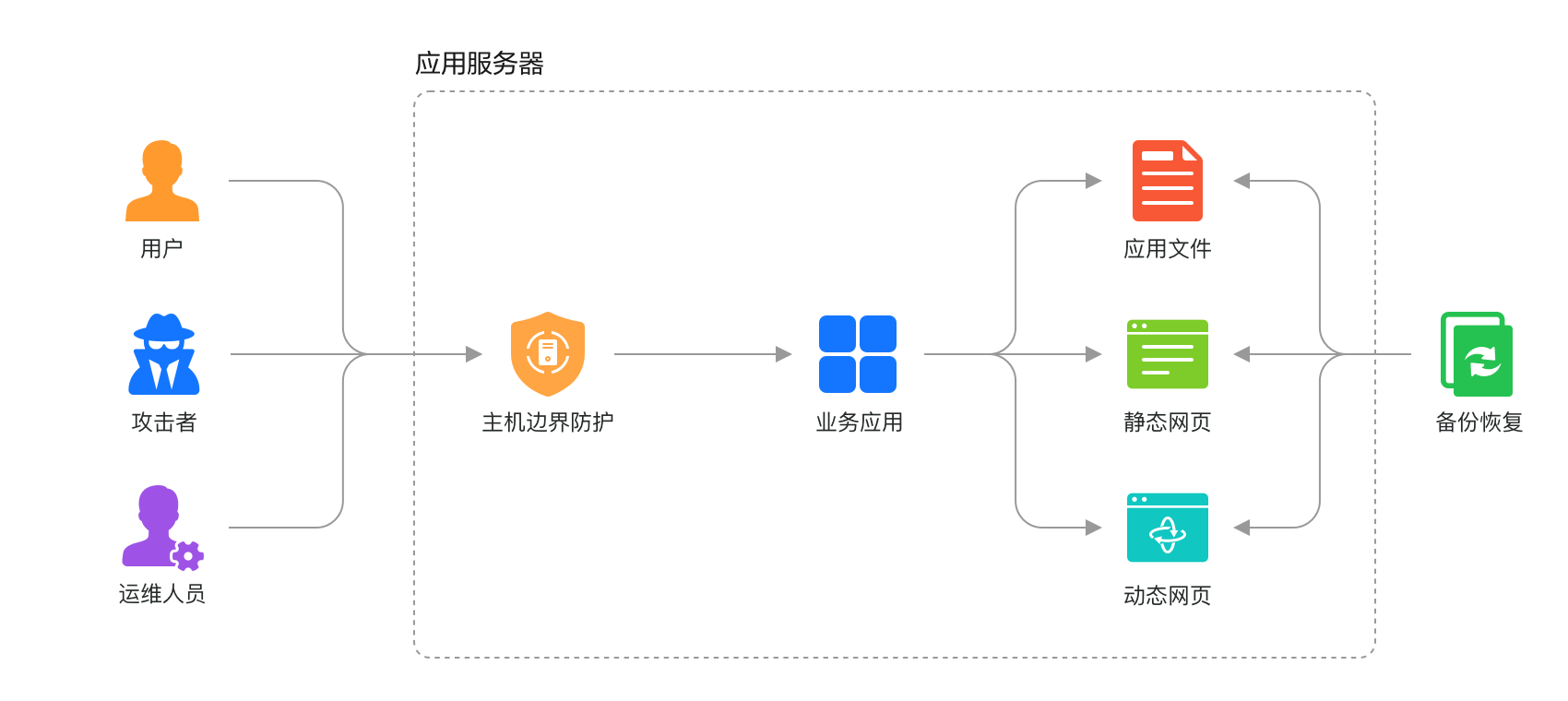
Huawei Cloud HSS devised a triple tamper-proofing strategy: for static webpages like .html, .txt, .js, it offers kernel-level drive technology based on the operating system and local and remote dual backup capabilities; for dynamic webpages, its proprietary RASP technology detects malicious website requests; and for 14 types of dynamic webpage attacks, including SQL injection and deserialization inputs, it provides attack source information for quick tampering source tracking.
Thirdly, container security.
With the proliferation of cloud-native technology, containers have become the mainstream method for application deployment. However, the dynamics, ephemerality, and complexity of the container environment pose new security challenges.
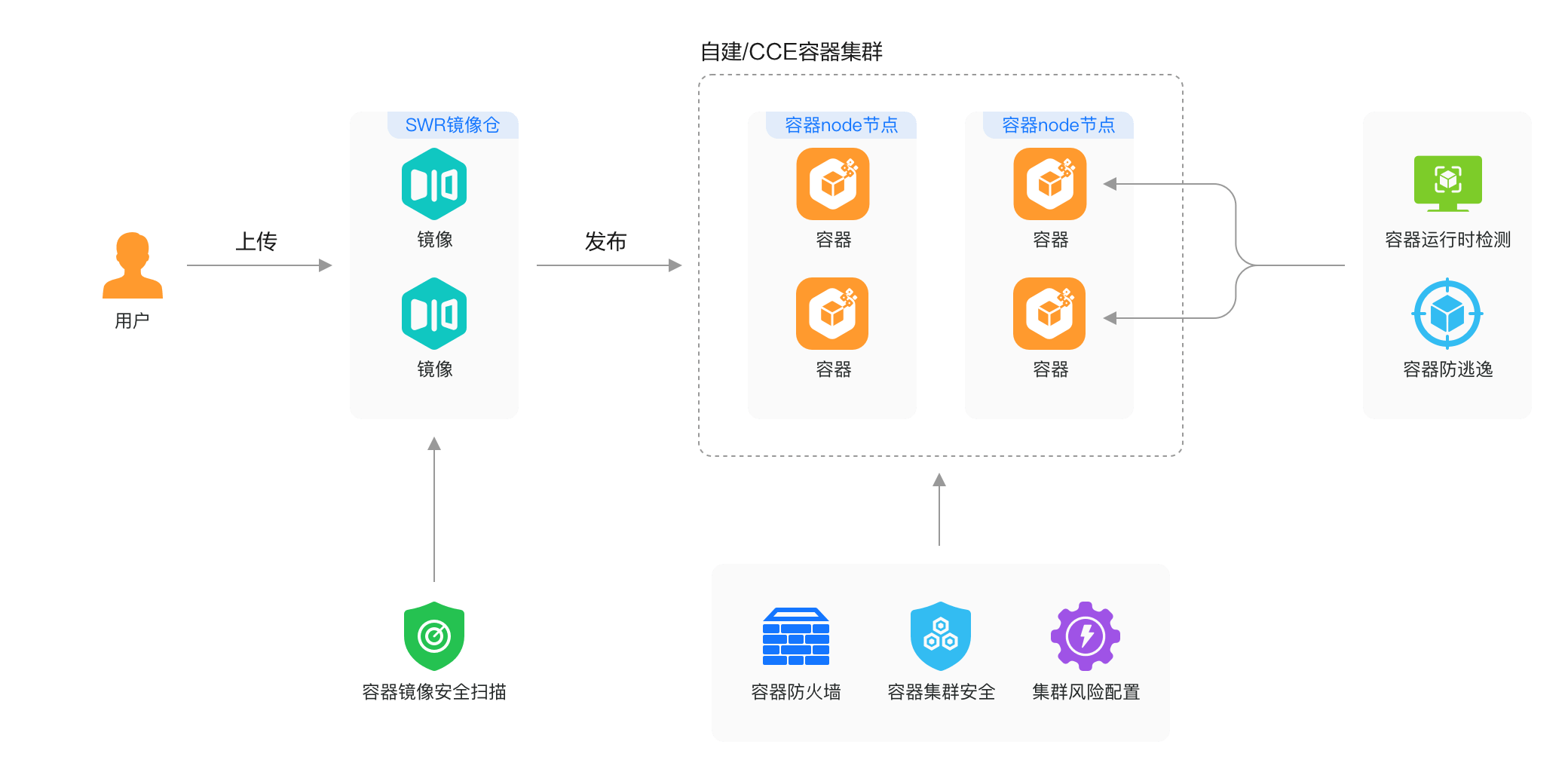
Huawei Cloud HSS provides lifecycle protection for Cloud Container Engine (CCE) and custom-built container clusters, addressing security needs such as container asset management, image security, cluster security, and runtime intrusion detection, including image security scanning, container cluster security, and container runtime security detection, helping enterprises establish a comprehensive container security protection system.
Fourthly, multi-cloud management.
The hybrid cloud architecture has become the norm for enterprise IT, with core businesses deployed across different cloud platforms, private clouds, and data centers. Managing host security in a heterogeneous environment is a significant challenge.
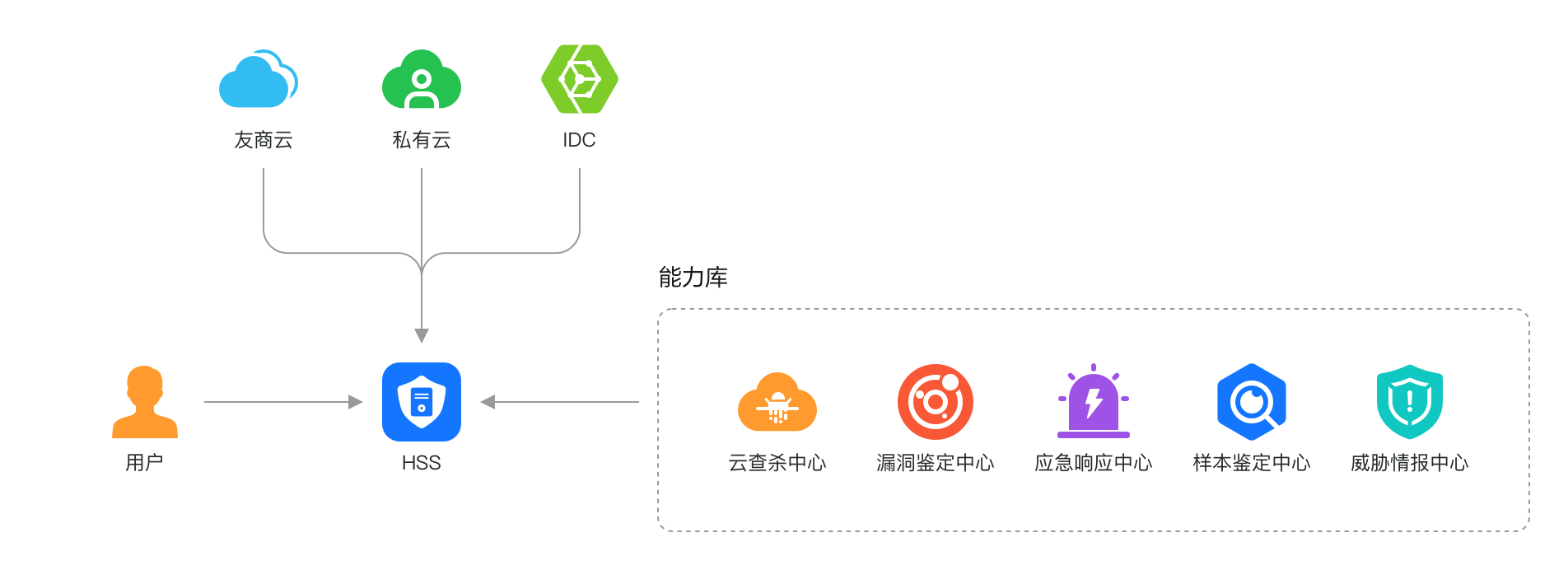
Huawei Cloud HSS's strategy is to offer unified protection, operation, and maintenance for servers, hosts, and containers, encompassing competitor clouds, private clouds, and IDCs, including vulnerability scanning and repair, baseline inspection and repair, ransomware protection, etc. Administrators can conduct unified security management and operations on Huawei Cloud, further reducing security management operating costs.
The enterprise host security service functions like an 'intelligent home security system.' Even if strangers attempt to evade security checks, the home security system, integrating functions like password locks, infrared cameras, smoke detectors, and emergency alarms, will detect and respond immediately.
In addition to network boundary security and enterprise host security, there's still a crucial piece of the puzzle to complete in an enterprise's security system: application layer protection.
As the primary portal for enterprises to provide external services, web applications are directly exposed to the internet and often become the 'main battlefield' for hacker attacks. These attacks include exploiting SQL injection vulnerabilities to steal, tamper with, or delete core database data; deploying massive malicious crawlers to steal original website content and valuable data; or bypassing authentication mechanisms through various means to directly access the management system.
Huawei Cloud's corresponding product is the Web Application Firewall (WAF), directly addressing three typical Web security protection scenarios, accurately identifying and blocking various types of application layer attacks.
Firstly, Web basic protection: establishing an OWASP TOP 10 'immune defense.'
The Open Web Application Security Project (OWASP) annually publishes the TOP 10 security threat list, considered the 'wind vane' in Web security.
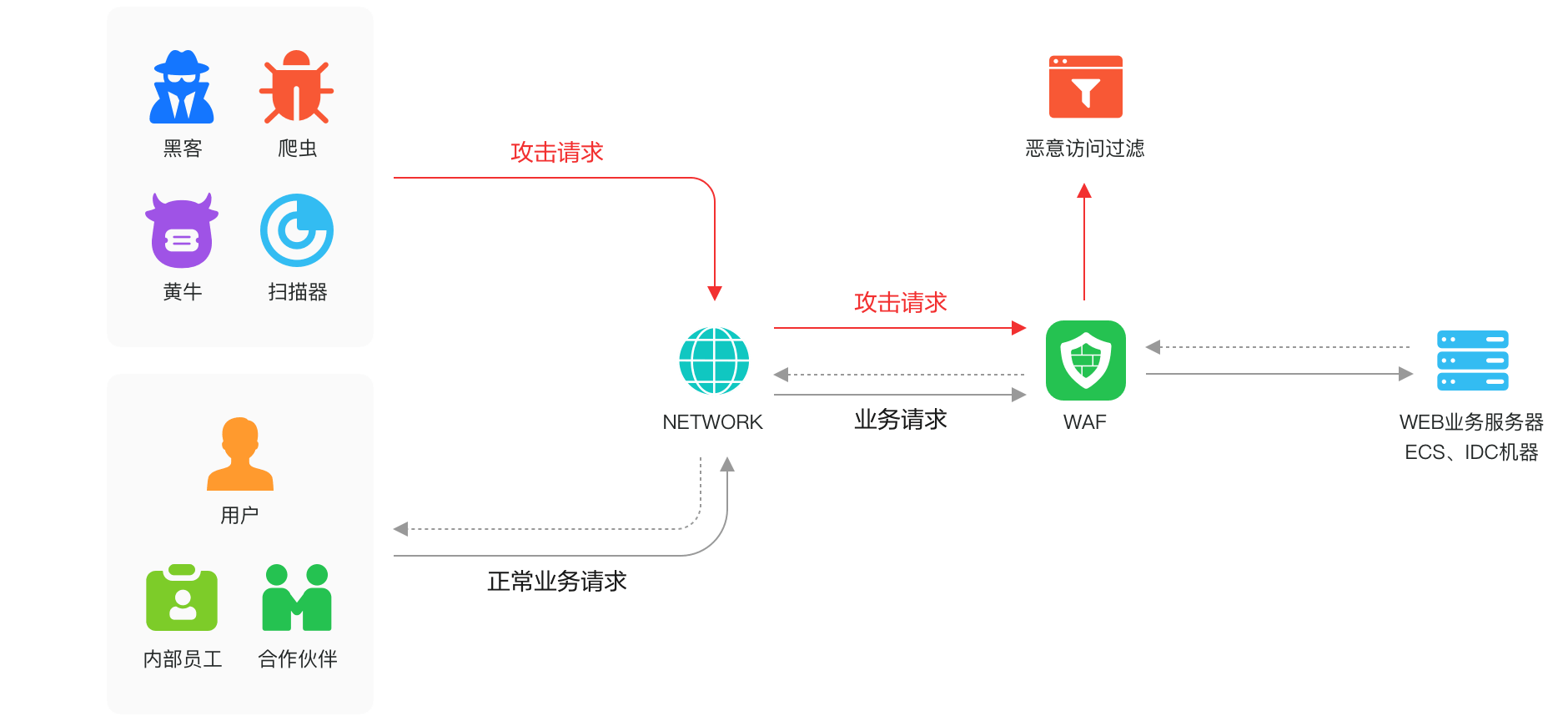
Huawei Cloud WAF's core mission is to comprehensively safeguard Web application security. For detecting and blocking common Web attacks like SQL injection, XSS cross-site scripting, Webshell uploads, directory (path) traversal, and file inclusion, it provides comprehensive attack protection, increasing the detection rate of OWASP TOP 10 threats by 40%. For emergency 0-Day vulnerabilities, a professional security operations team operates 24/7, enabling the repair of emergency 0-Day vulnerabilities within 2 hours, promptly issuing virtual patches in the cloud to swiftly contain cloud risks and ensure stable Web service operation.
Secondly, CC attack protection: intelligent recognition to ensure business continuity.
As a typical application-layer DDoS attack, CC attacks simulate numerous normal users, making them difficult for traditional traffic cleaning devices to distinguish, thereby continuously requesting resource-intensive application pages, exhausting server resources, and preventing normal user access.
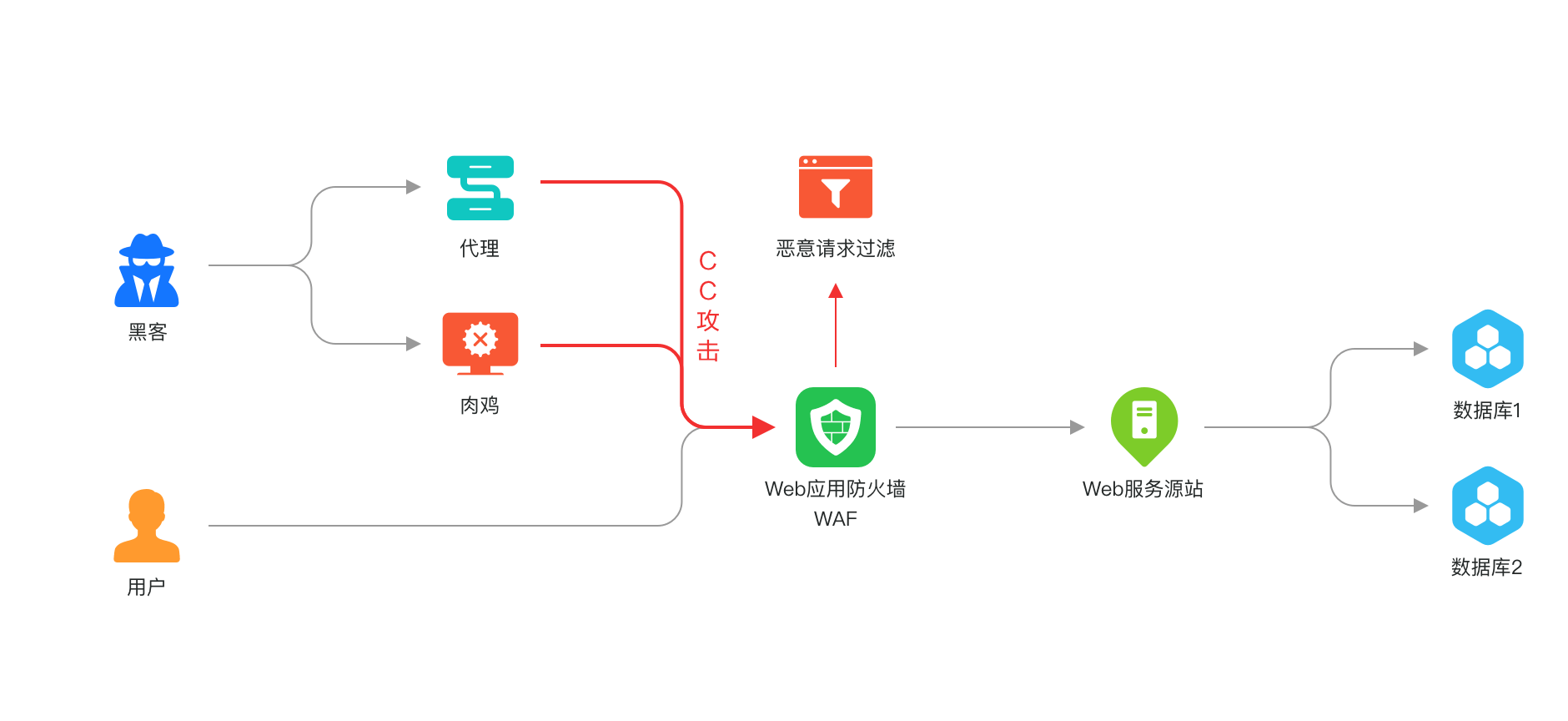
Huawei Cloud WAF can establish adaptable speed limit policies leveraging IP or Cookie field names, enabling precise identification and effective mitigation of CC attacks, thereby ensuring the seamless operation of your business. Additionally, it facilitates customization of blocking page content and type, empowering users to configure response actions and return page content tailored to business needs, thus accommodating the diverse requirements of your operations. For instance, through client fingerprint and behavior characteristics for human-machine differentiation, it effectively counteracts CC attacks without compromising the genuine user experience.
The third aspect is content security detection, functioning as the 'intelligent overseer' of website content.
When websites and new media accounts managed by governments, enterprises, and institutions feature illegal content such as pornography, politics, violence, or advertisements, it not only severely tarnishes their credibility and authoritative image but also risks igniting online public outcry, leading to irreparable negative societal impacts.
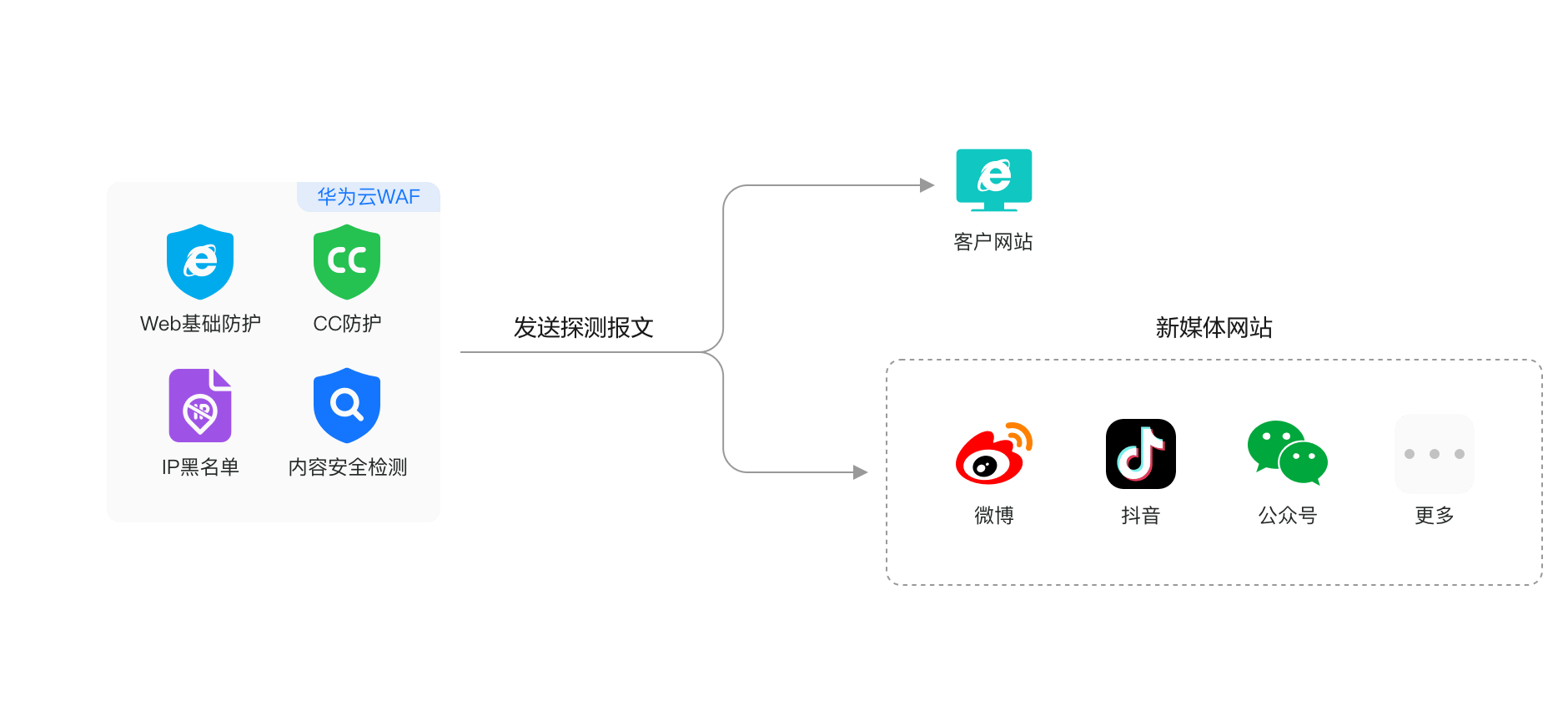
Huawei Cloud WAF's solution lies in its robust content security detection capabilities, which scrutinize text, images, audio, and video to intelligently ascertain the presence of pornographic, political, violent, inappropriate advertising, spam, and other unsuitable content. Upon detecting illegal content, it provides a comprehensive report to assist the operations team in swiftly locating and addressing the issue. Furthermore, it conducts normative reviews of text, images, audio, and video, encompassing typos, obscure characters, lexical and grammatical expressions, thereby enhancing the team's operational efficiency.
The Web Application Firewall (WAF) serves as the "intelligent steward" of application security, akin to the smart access control systems at building entrances, elevator identity recognition systems, and intelligent express delivery cabinet recognition systems, silently safeguarding the "ultimate line of defense".
In the face of escalating and pervasive security threats, isolated, passive defense measures are no longer sufficient. It is imperative to establish a systematic, in-depth defense mechanism and intelligent, continuous response system.
Huawei Cloud exemplifies this through a "layered defense strategy" to counter various threats: the Cloud Firewall (CFW) guards against large-scale internet attacks, the Host Security Service (HSS) ensures the integrity and stability of servers and containers, and the Web Application Firewall (WAF) meticulously filters malicious requests targeting core business applications. Each component performs its unique role while interacting seamlessly, collectively forming a solid, dependable, and intelligent security "iron triangle" for enterprises.
This underscores that security is no longer a reactive measure taken post-incident but an active capability integrated into business operations, consistently evolving to meet challenges head-on.